반응형
•Redhat 8.6 – IPA 4.9.8
•슈퍼 계정 이름이 admin이라 사전에 cluster admin 계정 삭제 권장
•계정 추가 테스트
[registry]
ipa down
yum module enable idm:DL1
yum distro-sync -y
yum module install idm:DL1/server -y
yum module install idm:DL1/dns -y
yum module install idm:DL1/adtrust -y
yum module install idm:DL1/{dns,adtrust} -y
yum module install idm:DL1/client -y
install
ipa-server-installThis step may take considerable amount of time, please wait..
Done.
Configuring client side components
This program will set up IPA client.
Version 4.9.8
Using existing certificate '/etc/ipa/ca.crt'.
Client hostname: registry.maru.ocp4.com
Realm: MARU.OCP4.COM
DNS Domain: maru.ocp4.com
IPA Server: registry.maru.ocp4.com
BaseDN: dc=maru,dc=ocp4,dc=com
Configured /etc/sssd/sssd.conf
Systemwide CA database updated.
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Could not update DNS SSHFP records.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring maru.ocp4.com as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
Please add records in this file to your DNS system: /tmp/ipa.system.records.x22cyoir.db
==============================================================================
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
UDP Ports:
* 88, 464: kerberos
* 123: ntp
2. You can now obtain a kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificates stored in /root/cacert.p12
These files are required to create replicas. The password for these
files is the Directory Manager password
The ipa-server-install command was successful
계정 확인
[root@registry ~]# kinit admin
Password for admin@MARU.OCP4.COM:
[root@registry ~]# ipa user-find admin
--------------
1 user matched
--------------
User login: admin
Last name: Administrator
Home directory: /home/admin
Login shell: /bin/bash
Principal alias: admin@MARU.OCP4.COM, root@MARU.OCP4.COM
UID: 1188200000
GID: 1188200000
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------
[bastion]
브라우저에서 확인
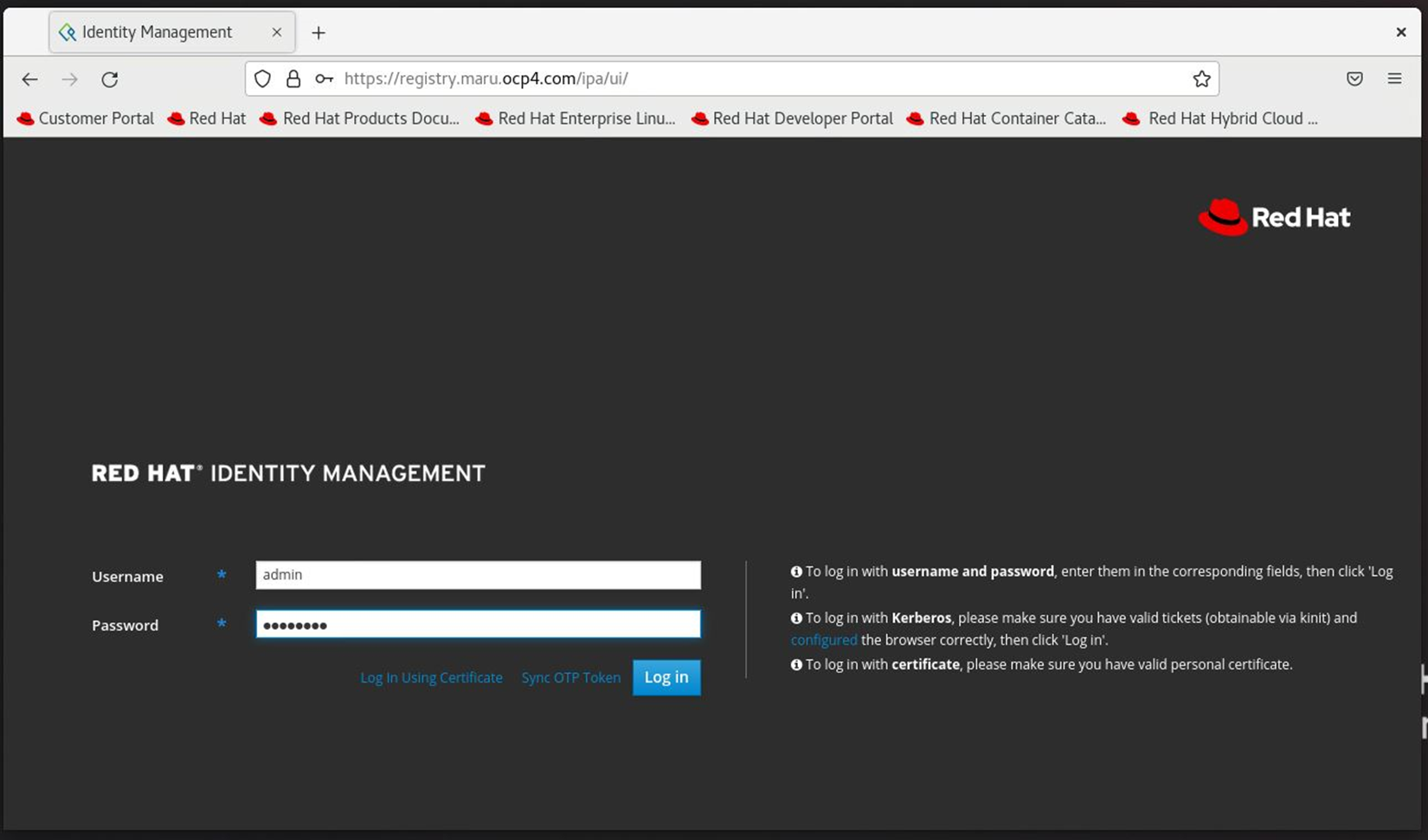
계정확인

TEST 계정 생성
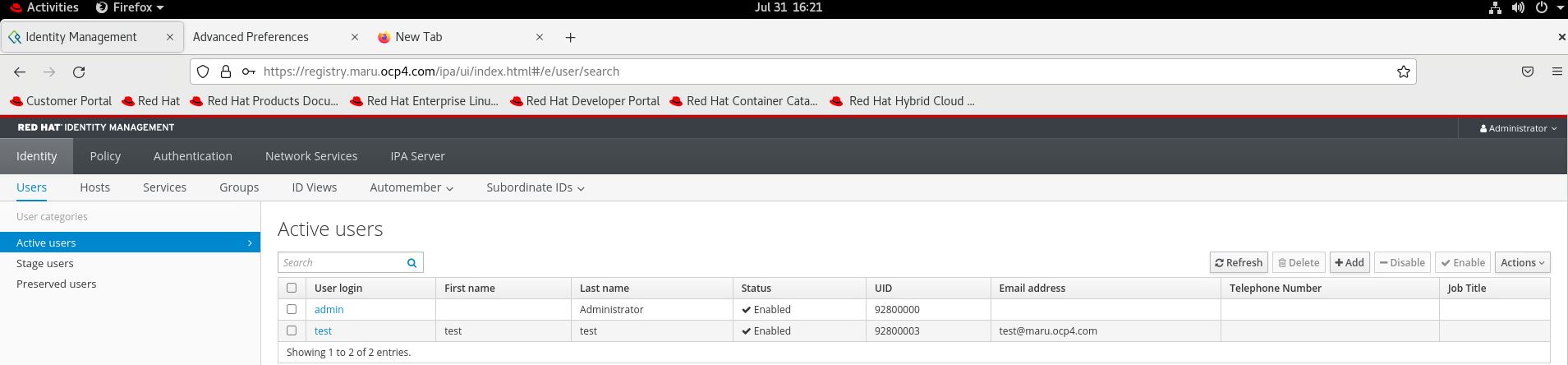
TEST를 위해 콘솔 로그인

Administration -> Cluset setting -> configure -> Oauth -> Add -> LDAP

인증서 다운
[root@bastion ~]# scp root@registry:/etc/ipa/ca.crt ./
Password:
ca.crt 100% 1643 795.5KB/s 00:00
LDAP 정보

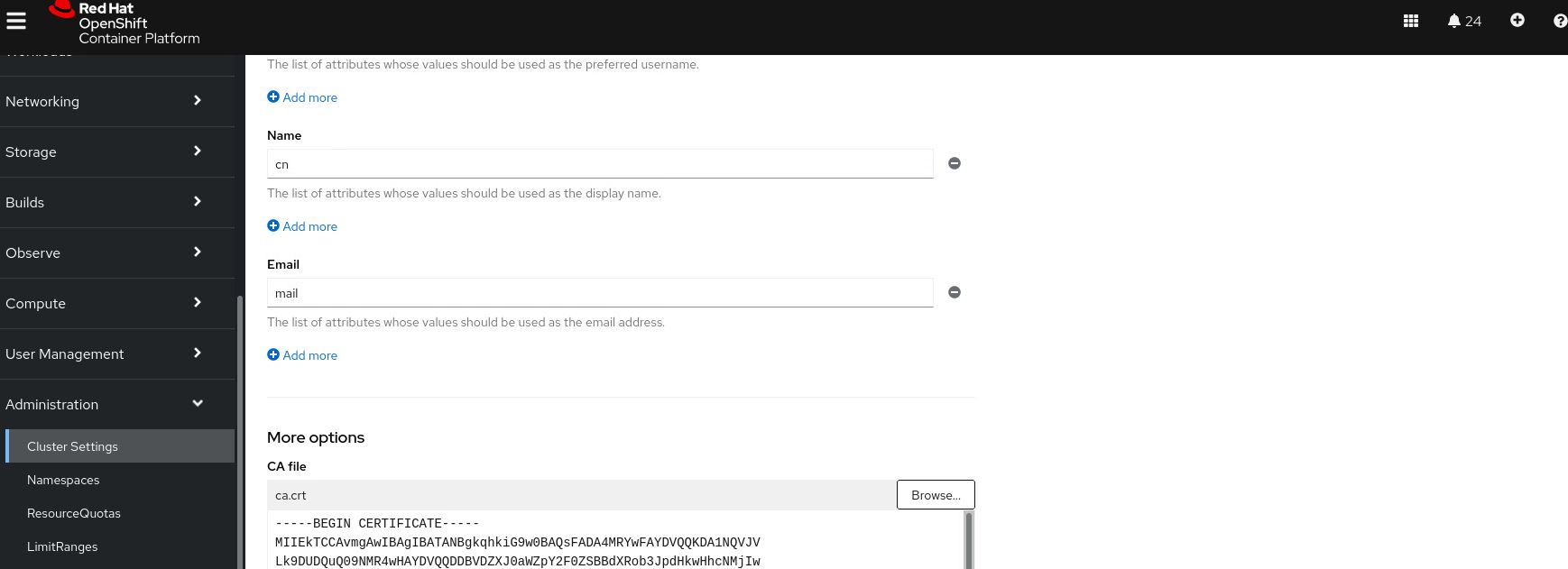
TEST 확인
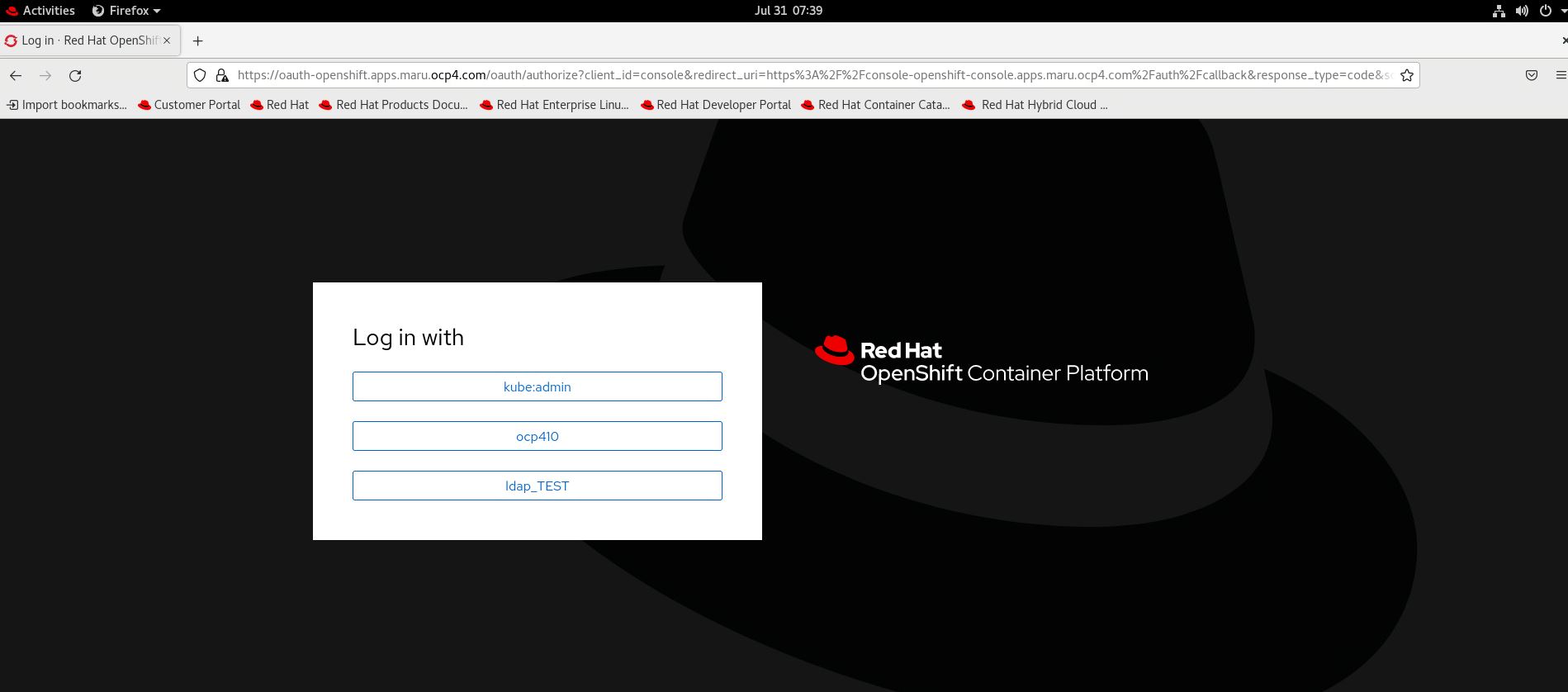
[registry]
확인
[root@registry ~]# oc get user
NAME UID FULL NAME IDENTITIES
admin 6684ade0-a335-46e0-a1c0-0f7c7c43126c ocp410:admin
test febf98b6-5afb-4f6b-bc09-01a99a7eccb1 test test ldap_TEST:dWlkPXRlc3QsY249dXNlcnMsY249Y29tcGF0LGRjPW1hcnUsZGM9b2NwNCxkYz1jb20
반응형
'CLOUD > Openshift' 카테고리의 다른 글
| OCP 4.10.23 설치(openshift) - 9. Rolling update, Restore and Backup (0) | 2022.08.31 |
|---|---|
| OCP 4.10.23 설치(openshift) - 8. GitLAB, 배포 (2) | 2022.08.30 |
| OCP 4.10.23 설치(openshift) - 6. pv (0) | 2022.08.28 |
| OCP 4.10.23 설치(openshift) - 5. infra node (0) | 2022.08.27 |
| OCP 4.10.23 설치(openshift) - 4. Install-config, bootstrap, master, worker (0) | 2022.08.26 |



